▸ AWS | LinkedIn Skill Assessment Quiz Solutions-1
Recommended AWS Courses:
- Udemy: Ultimate AWS Certified Developer Associate 2021 - NEW!
- Udemy: [NEW] Ultimate AWS Certified Cloud Practitioner - 2021
- Coursera: AWS Fundamentals Specialization
- Coursera: AWS Fundamentals: Going Cloud-Native
- LinkedIn: Learning Amazon Web Services (AWS) for Developers
- LinkedIn: AWS Essential Training for Developers
- edureka: AWS Certification Training for Solutions Architect
- Eduonix: AWS Certified DevOps Engineer: Get 3 Certifications 2021
-
What is the best practice for maintaining Windows EC2 instances and applying updates?
- Turn on auto update in Windows Update on each EC2 that is launched, or create your own AMI with this feature enabled and launch all of your EC2 instances from this AMI.
- Create a maintenance schedule that an employee must fill out each week confirming a visual inspection of each instance was conducted and which patches were applied.
- Use AWS Systems Manager Patch Manager to find an patch instances that require updates during a set maintenance window.
- Install Window Server Update Services on your primary Active Directory controller.
-
In addition to CloudFormation, you can use other orchestration tools to automate server formation and maintenance. Which tool is not an efficient choice for the orchestration of a large infrastructure?
- Chef
- Ansible
- Puppet
- Vagrant
-
What happens to a SQL Server RDS instance if the databases increase in size and go over the allocated space?
- RDS will automatically increase the allocated space by 10% and will send the AWS root account an email with resolution steps. Allocate more space to avoid overage charges.
- The database instance will report a STORAGE_FULL status and become inaccessible if the instance does not have enough remaining storage to operate. Allocate more space to the instance.
- SQL Server will close all existing connections to the databases and attempt to shrink its log files to reclaim storage space.
- RDS will automatically increase the allocated space by 5% and will continue to allocate new space up to 50% of the orginal allocated space. When storage space has increase 50%, RDS will automatically stop the instance to preserve data integrity.
-
You have a fleet of IoT devices that send telemetry to a server-side application provided by your IoT vendor for decoding a proprietary messaging format. The devices are provisioned to send telemetry reports to your server via UDP on port 6339. What is the best way scale this server as more Iot devices are added to your fleet?
- Use a Network Load Balancer to distribute the traffic across your servers. Use UDP health checks to determine if the server is available to receive traffic.
- Use Route 53 with HTTP health checks. Create an application on the server to report the readiness status of the vendor-provided server software to Route 53 via HTTP.
- Use Route 53 with UDP health checks. As you scale up, Route 53 wiwll route the traffic to the new servers if they pass the health checks.
- Use Application Load Balancer to distribute the traffic across your servers.
-
the outbound rules of a security group only allow traffic going to 0.0.0.0/0 on TCP Port 22 (SSH) and TCP port 3306 (MySQL). Review the inbound rules listed in the image below. What is the most important issue to fix with this security group configuration, for an Ubuntu EC2 instance acting as a web server?
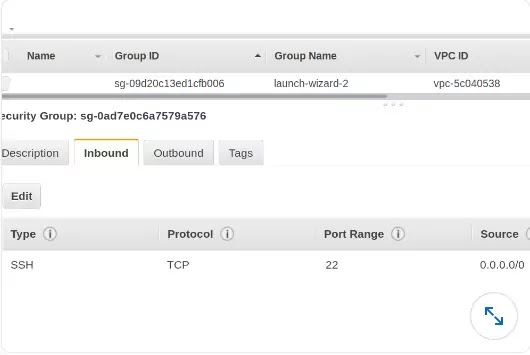
- The outbound rules block UDP port 53, so the server will not be able to resolve any DNS lookups.
- The outbound rules do not allow for HTTP traffic to leave the instance, so inbound HTTP requests will fail because the clients will never get HTTP responses.
- The incoming SSH port should not be open to the public. Limit SSH to a single IP address or IP range of controlled addressed, or use a VPN to access the VPC for this server.
- The all incoming TCP ports are exposed, which overrides the HTTP and SSH rules and exposes all TCP ports to the public internet.
-
An EC2 instance running a WordPress site keeps getting hacked, even though you have restored the server several times and have patched WordPress. What AWS service can help you detect and prevent further attacks?
- CloudWatch
- GuardDuty
- Shield
- Security Advisor
-
A nontechnical client wants to migrate a WordPress site to AWS from a private server managed by a third-party hosting company. Which AWS service should you recommend to migrate the site to?
- CloudFront
- An EC2 instance launched from the official WordPress AMI
- S3
- Lightsail
-
Your company has on-premise servers with an existing onsite backup solution that also replicates backups to another campus on the other side of the country with its own on-site backup solution. You have been asked to create a third level of redundancy by also storing these backups in the cloud. In the event of a primary and secondary backup failure, your boss wants to know that the cloud backups can be accessible as fast as possible to reduce downtime during the recovery. What S3 storage class do you recommend for cost and performance?
- S3 Standard
- S3 Intelligent-Tiering
- S3 Glacier
- S3 One Zone-Infrequent Access
-
Which big data store will let you store large streams of user activity data coming from both web and mobile applications?
- Neptune
- Aurora
- RDS for SQL Server
- Redshift
-
What option is best for Auto Scaling your EC2 instances for predictable traffic patterns?
- scale based on a schedule
- manual scaling
- scale based on demand
- maintain current levels at all times
-
You are migrating an on-premise RabbitMQ cluster into AWS. Which migration path should you choose for ease of both maintenance and deployment?
- Rewrite the parts of your application that use RabbitMQ to use SQS.
- Launch a RabbitMQ cluster with EC2 instances using a supported AMI.
- Rewrite the parts of your application that use RabbitMQ to use Kinesis.
- Rewrite the parts of your application that use RabbitMQ to use Amazon MQ.
-
When creating a new RDS instance, what does the Multi-AZ option do?
- replicates backups of your database to S3 and makes them available across regions to prevent against any data loss
- creates a second passive database instance within the same region that will become the primary database during a failover
- creates a highly available database cluster that will host your database cluster in at least two regions
- creates another database instance in another region and keeps a hot standby active to failover to during regional failures
-
What is the best EC2 instance class for a server that continuously has a heavy CPU load?
- C5
- T2
- R5
- H1
-
Your application performance management (APM) system can read the status of your CloudWatch monitors and perform scripted actions. When the CloudWatch metric StatusCheckFailed enters a failed state (a value of 1), you would like your APM to automatically repair the instance. Which script do you use?
- A
aws ec2 stop-instances --instance-ids i-0b263919b6498b123 aws ec2 start-instances --instance-ids i-0b263919b6498b123- B
aws ec2 reboot-instances --instance-ids i-0b263919b6498b123- C
aws ec2 reboot-instances --instance-ids i-0b263919b6498b123 wait 30 aws ec2 start-instance --instance-ids i-0b263919b6498b123- D
aws ec2 reboot-instances --instance-ids i-0b263919b6498b123 aws ec2 start-instances --instance-ids i-0b263919b6498b123
-
What is wrong with the third incoming security group rule, which allows all traffic from sg-269afc5e to go to an Ubuntu EC2 instance configured as a web server?
- All traffic on all ports is being denied into this instance, which overwrites the HTTP rule and makes it redundant.
- The instance was launched with the default security group, but there is no way for an administrator to SSH into the instance.
Add another rule that allows for SSH access from a secured source, such as a single IP or a range of managed IP addresses. - There is nothing wrong with this security group rule. Assuming that sg-269afc5e is applied to other resources that are properly
secured, this rule allows all traffic to pass through that is also assigned security group sg-269afc5e. - ?> All traffic on all ports are allowed into this instance. This exposes the instance to all public internet traffic and
overwrites the incoming HTTP rule.
-
You have a VPC that has a public and private subnet. There is a NAT gateway in the public subnet that allows instances in the private subnet to access the internet without having public exposure outside of the VPC. What should the routing tables be for the private subnet?
- A
Destination 1: 10.0.0.0/16, Target 1: local; Destination 2: 0.0.0.0/0, Target 2: nat-09b4832- B
Destination 1: 10.0.0.0/24, Target 1: local; Destination 2: 0.0.0.0/0, Target 2: igw-b2ff47d6- C
Destination 1: 10.0.0.0/24, Target 1: subnet-1948ba2; Destination 2: 0.0.0.0/0, Target 2: nat-09b4832- D
Destination 1: 10.0.0.0/16, Target 1: vpc-12bd09ac2; Destination 2: 0.0.0.0/0, Target 2: igw-b2ff47d6
-
To comply with auditing requirements of some compliance standards, which AWS tool can be enabled to maintain an audit log of access and changes to your AWS infrastructure?
- CloudTrail
- CloudWatch
- AWS Audit and Compliance Tool
- GuardDuty
-
You have an application that generates long-running reports, stores them in an S3 bucket, and then emails the user who requested the report with a link to download it. What is the best practice for storing the report data in S3?
- Create a public S3 bucket. When your application creates the report object in S3, generate two randomly generated long folder names and place the file within the deepest subfolder. Set the retention policy on the object to one hour and email this link to the user. The link will be active for one hour.
- Create a public S3 bucket. Use a hash of the user’s email address and the date and time the report was requested to generate a unique object name. Email this link to the user and have a scheduled task run within your application to remove objects that are older
than seven days. - Create a private S3 bucket. The link in the email should take the user to your application, where you can verify the active user session or force the user to log in. After verifying the user has rights to access this file, have the application retrieve the object from S3 and return it in the HTTP response. Delete the file from the S3 bucket after the request is completed.
- Create a private S3 bucket. The link in the email should take the user to your application, where you can verify the active user session or force the user to log in. Set the report object in S3 to public. Show the user a “Download” button in the browser that links to the public object.
-
When sending a large volume of email through SES, what is the most important set of metrics to monitor?
- your complaint and bounce rates
- opens and clicks
- clicks and deliveries
- sending volume over the past 15 minutes and over one day to watch for billing spikes
-
You are going to host an application that uses a MySQL database. Which database should you select if you don’t want to manage scaling or database administration tasks?
- Launch an AMI image from the marketplace containing a preconfigured MySQL server.
- Aurora
- RDS for MySQL
- Redshift
-
A form in web application is sending sign-up data to “http://example.com/signup/new?source=web” and this data needs to be handled by an ECS service behind Application Load Balancer (ALB). Which ALB rule will route this request?
- A
IF (all match) Path is /signup* Query string is signup:new Then Forward to ecs-cluse-service <there is a typo - yes!- B
IF (all match) Path is /sign/new/& Query request method is POST Then Forward to ecs-cluse-service- C …One more with POST
- D …Only one with Get
-
Which AWS service can host the web application server for a WordPress site?
- S3
- Elastic BeanStalk
- ElasticCache
- CloudFront
-
What does the following AWS CLI
create-servicecommand for ECS do?aws ecs create-service \ --cluster production \ --service-name rest-api \ --task-definition rest-api:1 \ --desired-count 2 \ --launch-type "FARGET" \ --network-configuration \ "awsvpcConfiguration={subnets=[subnet-0b29129ab],securityGroups=[sg-0b29129ab]}"- changes the security groups of the running rest-api task
- creates a cluster called production and launches two containers into Farget with the rest-api task definition
- launches two containers onto Farget into the existing production cluster using the rest-api task definition
- creates a service definition for the rest-api task; put two containers on the production cluster when launched ecs-cli up command
-
You want to make your public API quickly accessible from all regions. What is the best way to do this?
- Create a single API gateway endpoint in a central region.
- Create a private API gateway endpoint for each region.
- Create a regional API gateway endpoint for each region.
- Create edge-optimized API gateway endpoints and deploy them to a CloudFront network.
-
What type of data solution should you use for data coming from nonrelational and relational data from IoT devices, websites, mobile apps, etc.?
- Amazon DynamoDB
- AWS Lake Formation
- Amazon Redshift
- Amazon Aurora
CREDITS: (Source)
&
Click here to see solutions for all Machine Learning Coursera Assignments.
&
Click here to see more codes for Raspberry Pi 3 and similar Family.
&
Click here to see more codes for NodeMCU ESP8266 and similar Family.
&
Click here to see more codes for Arduino Mega (ATMega 2560) and similar Family.
Feel free to ask doubts in the comment section. I will try my best to answer it.
If you find this helpful by any mean like, comment and share the post.
This is the simplest way to encourage me to keep doing such work.
- APDaga DumpBox



